News & Briefings
Get the latest news and SOF commentary here. Your source for all news SOF since 2017.

In an era of strategic competition, America’s adversaries are engaged in persistent operations against US interests in a spectrum of low-intensity conflict frequently referred to as the “gray zone”. The legal and bureaucratic limitations for the use of power that have served America well in the past are being effectively exploited by peer and near-peer adversaries. The US should proactively aim to divert, distract, and degrade enemy capabilities through restructuring the US Special Operations Forces’ (SOF) mission set to operate against its adversaries in the gray zone. Counterinsurgency and Foreign Humanitarian Assistance should be removed from SOF’s Core Activities and given to other entities, and Persistent Gray Zone Operations (PGZO) should be added to SOF’s Core Activities. PGZO will seek to deter enemy provocations by lowering the threshold for attribution of subnational actors’ operations to the foreign states whose interests they serve, increasing SOF’s information warfare capability to project US messaging into adversarial countries, and fomenting instability in diverse regions where the US seeks to gain an asymmetric advantage over its adversaries.

Department of Defense Instruction 3000.07 defines Irregular Warfare with ambiguous criteria, including indirect approaches and asymmetric activities, which are also characteristic of conventional warfare. This lack of differentiating criteria complicates planning and approval processes. To provide a clearer distinction, this article proposes adding a complementary criterion, the level of state stewardship (state authority, entitlement, and responsibility), to differentiate state, or conventional, forces from irregular forces such as private militias, criminals, and disenfranchised groups. This model also proposes a model for visualizing and categorizing operations and activities within the spectrum of irregular and conventional warfare. Recognizing the presence of irregular forces in a contest will allow commanders to better apply the specific laws, authorities, and doctrines for supporting or targeting non-state forces.

Afghanistan remains relevant to the United States in the context of Great Power Competition. While China assumed a major role in Afghanistan after the U.S. withdrawal, its promises of economic performance on mineral extraction contracts continue to underperform financially. The U.S. has an opportunity to compete for strategic minerals by changing where value is gained in the strategic supply chain.
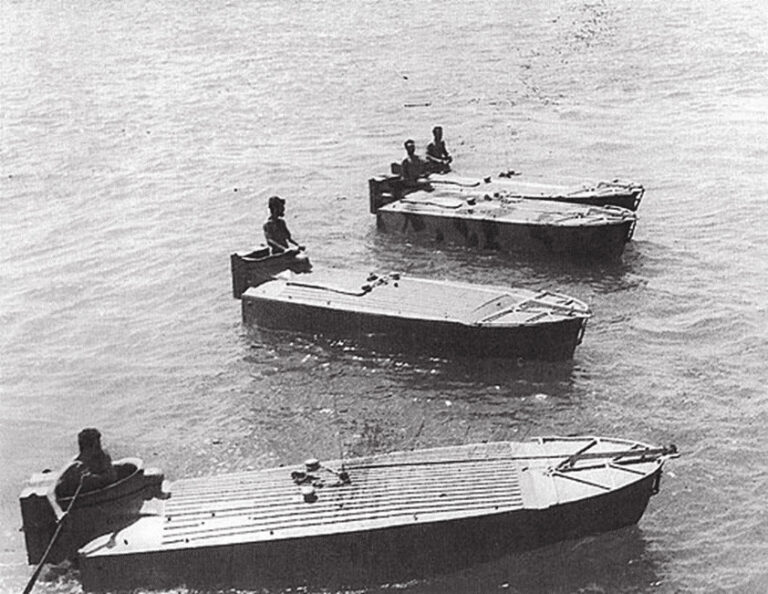
In an era of renewed strategic rivalry, the maritime domain has become a central arena for irregular threats—coercive but deniable, asymmetric yet strategically consequential. Adversaries such as China, Iran, Russia, and North Korea increasingly employ maritime militias, legal warfare, cyber-enabled coercion, and proxies to exert influence and challenge the international order below the threshold of conventional war. Their actions not only pressure larger maritime powers but also demonstrate to smaller maritime nations, including U.S. allies, how irregular methods can be leveraged to offset conventional disadvantages.

Contemporary security discourse is frequently captured by a false narrative on new forms of warfare. The recent emergence of the term “cognitive warfare” is a symptom of this misconception, suggesting a novel evolution in warfare that does not exist. This form of non-military aggression was not unknown to us; on the contrary, at the onset of the Cold War, the United States profoundly understood the critical importance of public opinion to national security, both domestically and within nations abroad. American leadership recognized that the Soviet Union, and later China, waged political warfare that specifically targeted these populations to undermine the United States without firing a shot.

This article examines ubiquitous technical surveillance (UTS) as the operationalized manifestation of unrestricted warfare in contemporary strategic competition, arguing that it collapses normative assumptions of access, attribution, and initiative. It contends that the renewal of irregular warfare lies in signature reduction as a counteroffensive gray zone doctrine that preserves freedom of maneuver by centering human operational judgment under pervasive surveillance conditions.
No results found.
Stay Up To Date
Subscribe to Our Newsletter and Stay Up to Date with the Latest Special Operations Forces Support News and Events
